Security Policies
Configure and enforce security policies across your organization. Define rules for agent behavior, access control, and compliance requirements. Monitor policy violations in real-time and receive automated alerts when agents operate outside defined boundaries.
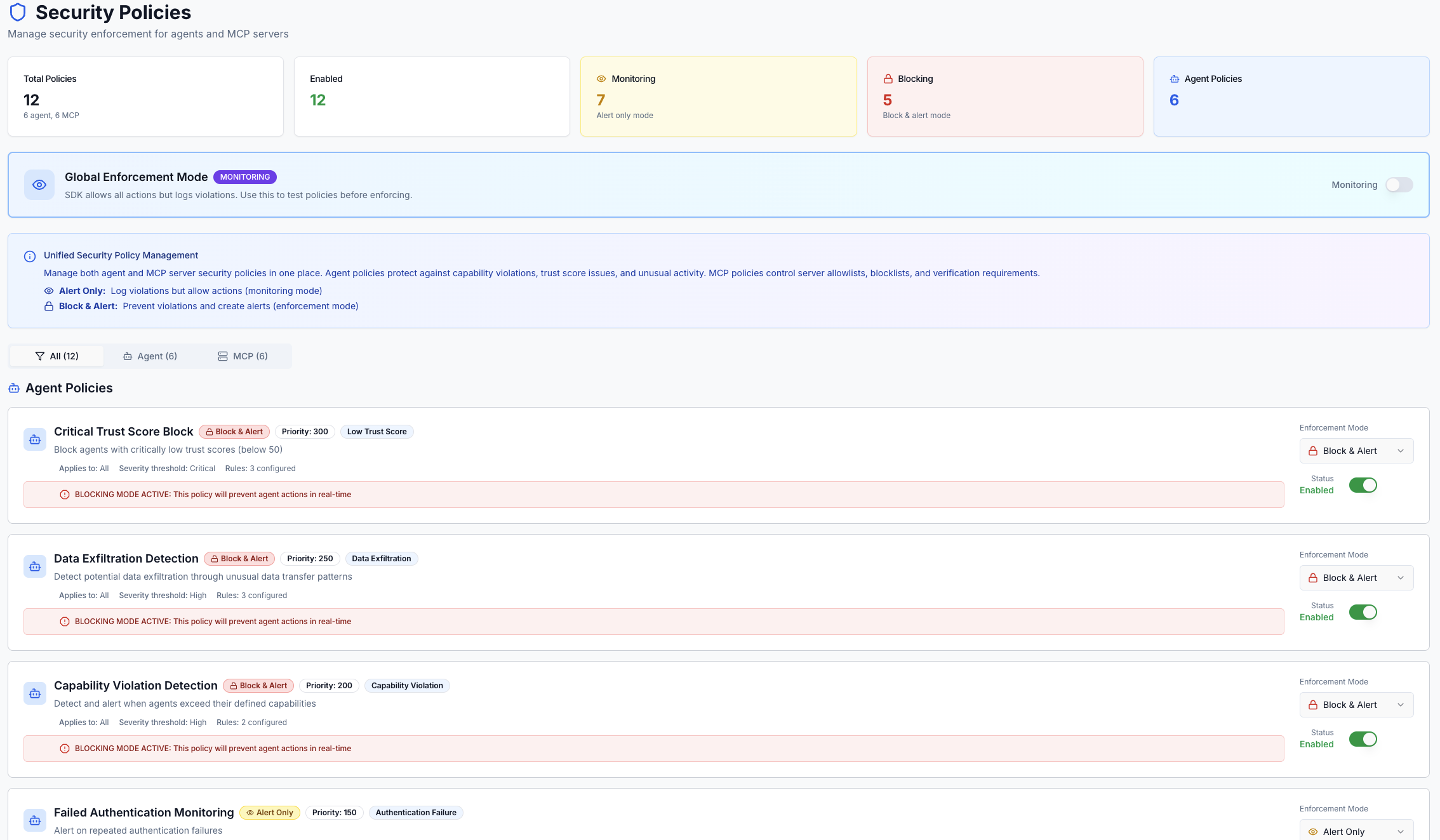
Security: Security policies are evaluated in real-time during agent operations. Configure policies once and enforce them automatically across all agents.
Policy Types
✨ Recently Implemented: Three advanced policy evaluation features are now available with full audit log integration and real-time enforcement.
Unusual Activity Detection
NEWML-powered detection of abnormal agent behavior patterns and security threats.
- • API rate spike detection with configurable thresholds
- • Off-hours access monitoring (business hours enforcement)
- • Unusual access pattern detection (diverse resource tracking)
- • Time-window based analysis (configurable minutes)
Configuration Drift Monitoring
NEWTrack and alert on unauthorized changes to agent configuration and permissions.
- • Capability change detection (permission modifications)
- • Public key rotation tracking with approval workflow
- • Permission escalation detection for dangerous capabilities
- • Historical capability comparison
Unauthorized Access Control
NEWEnforce strict access controls with IP restrictions, time-based rules, and resource-level permissions.
- • IP-based restrictions with whitelist and wildcard support
- • Time-based access control (day-of-week and hour restrictions)
- • Resource-level access control with pattern matching
- • Action-level granular permissions
Access Control
Define who can access what resources and under which conditions.
- • Role-based access control (RBAC)
- • Time-based access restrictions
- • IP allowlisting/denylisting
- • Geographic restrictions
Data Protection
Protect sensitive data with encryption and access policies.
- • Data encryption requirements
- • PII/PHI handling rules
- • Data retention periods
- • Secure deletion policies
Rate Limiting
Prevent abuse with configurable rate limits and throttling.
- • API call rate limits
- • Per-agent quotas
- • Burst protection
- • Adaptive throttling
Audit & Logging
Comprehensive logging and audit trail for all policy evaluations.
- • Policy evaluation logging
- • Violation tracking
- • Historical analysis
- • Export for compliance
MCP Server Policies
Control which MCP servers your agents can connect to with these specialized policies. MCP policies help enforce security boundaries for Model Context Protocol integrations.
MCP Minimum Trust Score
Alert when MCP servers fall below the minimum trust score threshold (default: 60). Helps identify potentially risky MCP integrations.
MCP Capability Requirements
Ensure MCP servers declare required capabilities and do not expose dangerous ones. Enforces capability boundaries for security.
Trusted MCP Server Domains
Allow MCP servers only from trusted domains (localhost, internal networks, major cloud providers).
Blocked MCP Domains
Block MCP servers from known malicious or untrusted domains. Connections are blocked in real-time.
High-Risk MCP Server Block
Block connections to MCP servers with critically low trust scores (below 30). Requires verification.
Global Enforcement Mode
Key Concept: Global Enforcement Mode determines whether security policies can actually block actions. Individual policy settings (Alert Only vs Block & Alert) are evaluated, but blocking only occurs when Global Enforcement Mode is set to STRICT.
MONITORING Mode
Observe and learn without disrupting agent operations. All actions are allowed regardless of individual policy settings.
Behavior:
- ✓All agent actions are allowed
- ✓Policies are still evaluated
- ✓Violations generate alerts
- ✓All actions are logged for audit
- ✗Policy blocking decisions are overridden
Recommended for: Development, testing, gradual rollout, and learning agent behavior patterns.
STRICT Mode
Full enforcement of all security policies. Actions that violate blocking policies are denied in real-time.
Behavior:
- ✓Policies are fully enforced
- ✓"Block & Alert" policies block actions
- ✓Violations generate alerts
- ✓All actions are logged for audit
- ✓Unauthorized capabilities are blocked
Recommended for: Production environments where security enforcement is critical.
Policy Evaluation Flow
┌─────────────────────────────────────────────────────────────┐
│ Action Requested │
└─────────────────────────────────────────────────────────────┘
│
▼
┌─────────────────────────────────────────────────────────────┐
│ Evaluate Security Policies │
│ (Capability Violation, Trust Score, Data Exfiltration...) │
└─────────────────────────────────────────────────────────────┘
│
▼
┌───────────────────┐
│ Policy says BLOCK │
└───────────────────┘
│
┌───────────────────┴───────────────────┐
│ │
▼ ▼
┌─────────────────────┐ ┌─────────────────────┐
│ MONITORING Mode │ │ STRICT Mode │
│ ───────────────── │ │ ───────────────── │
│ ✓ Allow action │ │ ✗ Block action │
│ ✓ Create alert │ │ ✓ Create alert │
│ ✓ Log violation │ │ ✓ Log violation │
└─────────────────────┘ └─────────────────────┘Individual Policy Modes
Each individual policy can be configured with one of these modes. However, remember that blocking only takes effect when Global Enforcement Mode is set to STRICT.
Alert Only
Policy violations generate alerts but do not block actions. Use for monitoring before enforcing.
Block & Alert
Policy violations block the action in real-time and generate alerts. Only effective when Global Mode is STRICT.
API Endpoints
List All Security Policies
curl -X GET https://api.opena2a.org/v1/admin/security-policies \
-H "Authorization: Bearer YOUR_TOKEN"{
"policies": [
{
"id": "policy_abc123",
"name": "Maximum Trust Score Required",
"description": "Agents must maintain trust score above 70",
"policy_type": "trust_score",
"enabled": true,
"severity": "high",
"conditions": {
"min_trust_score": 70,
"evaluation_frequency": "continuous"
},
"actions": {
"on_violation": "suspend_agent",
"notify_admins": true
},
"created_at": "2024-01-15T10:00:00Z",
"updated_at": "2024-01-15T10:00:00Z"
},
{
"id": "policy_def456",
"name": "Rate Limit Enforcement",
"description": "Limit agents to 1000 requests per hour",
"policy_type": "rate_limit",
"enabled": true,
"severity": "medium",
"conditions": {
"max_requests_per_hour": 1000,
"window_size": "1h"
},
"actions": {
"on_violation": "throttle",
"notify_admins": false
},
"created_at": "2024-01-15T10:00:00Z",
"updated_at": "2024-01-15T10:00:00Z"
}
],
"total": 2
}Get Policy by ID
curl -X GET https://api.opena2a.org/v1/admin/security-policies/policy_abc123 \
-H "Authorization: Bearer YOUR_TOKEN"Create Security Policy
curl -X POST https://api.opena2a.org/v1/admin/security-policies \
-H "Authorization: Bearer YOUR_TOKEN" \
-H "Content-Type: application/json" \
-d '{
"name": "IP Allowlist Policy",
"description": "Only allow agents from approved IP ranges",
"policy_type": "ip_allowlist",
"enabled": true,
"severity": "critical",
"conditions": {
"allowed_ips": [
"192.168.1.0/24",
"10.0.0.0/8",
"172.16.0.0/12"
],
"block_vpn": true
},
"actions": {
"on_violation": "block_request",
"notify_admins": true,
"log_violation": true
}
}'{
"policy": {
"id": "policy_xyz789",
"name": "IP Allowlist Policy",
"description": "Only allow agents from approved IP ranges",
"policy_type": "ip_allowlist",
"enabled": true,
"severity": "critical",
"conditions": {
"allowed_ips": [
"192.168.1.0/24",
"10.0.0.0/8",
"172.16.0.0/12"
],
"block_vpn": true
},
"actions": {
"on_violation": "block_request",
"notify_admins": true,
"log_violation": true
},
"created_at": "2024-01-15T12:00:00Z",
"updated_at": "2024-01-15T12:00:00Z"
}
}Update Security Policy
curl -X PUT https://api.opena2a.org/v1/admin/security-policies/policy_xyz789 \
-H "Authorization: Bearer YOUR_TOKEN" \
-H "Content-Type: application/json" \
-d '{
"name": "Updated IP Allowlist Policy",
"description": "Updated to include additional IP ranges",
"conditions": {
"allowed_ips": [
"192.168.1.0/24",
"10.0.0.0/8",
"172.16.0.0/12",
"203.0.113.0/24"
],
"block_vpn": false
}
}'Toggle Policy (Enable/Disable)
curl -X PATCH https://api.opena2a.org/v1/admin/security-policies/policy_xyz789/toggle \
-H "Authorization: Bearer YOUR_TOKEN" \
-H "Content-Type: application/json" \
-d '{
"enabled": false
}'{
"policy": {
"id": "policy_xyz789",
"name": "Updated IP Allowlist Policy",
"enabled": false,
"updated_at": "2024-01-15T13:00:00Z"
},
"message": "Policy disabled successfully"
}Delete Security Policy
curl -X DELETE https://api.opena2a.org/v1/admin/security-policies/policy_xyz789 \
-H "Authorization: Bearer YOUR_TOKEN"{
"message": "Security policy deleted successfully",
"policy_id": "policy_xyz789"
}Policy Configuration Examples
Trust Score Enforcement
{
"name": "Minimum Trust Score",
"policy_type": "trust_score",
"conditions": {
"min_trust_score": 60,
"check_frequency": "hourly"
},
"actions": {
"on_violation": "alert",
"notify_admins": true
}
}Data Access Control
{
"name": "PII Access Control",
"policy_type": "data_access",
"conditions": {
"data_types": ["pii", "phi"],
"requires_approval": true,
"max_records_per_request": 100
},
"actions": {
"on_violation": "block",
"log_attempt": true
}
}Best Practices
- ✓Start with monitoring mode: Enable new policies in alert-only mode before enforcing blocks to understand impact
- ✓Use severity levels: Classify policies by severity (critical, high, medium, low) for appropriate responses
- ✓Regular policy reviews: Review and update policies quarterly to align with business requirements
- ✓Test before production: Test policy changes in staging environment before deploying to production
- ✓Document exceptions: Maintain documentation for policy exceptions and their business justification
Available Endpoints
| Method | Endpoint | Description |
|---|---|---|
| GET | /admin/security-policies | List all security policies |
| GET | /admin/security-policies/:id | Get specific policy |
| POST | /admin/security-policies | Create new policy |
| PUT | /admin/security-policies/:id | Update existing policy |
| DELETE | /admin/security-policies/:id | Delete policy |
| PATCH | /admin/security-policies/:id/toggle | Enable/disable policy |