Alert Management
Real-time security alerts and notifications for your AI agent ecosystem. Monitor suspicious activities, capability violations, trust score drops, and security policy breaches. Configure alert rules, set severity thresholds, and integrate with your existing incident response workflows.
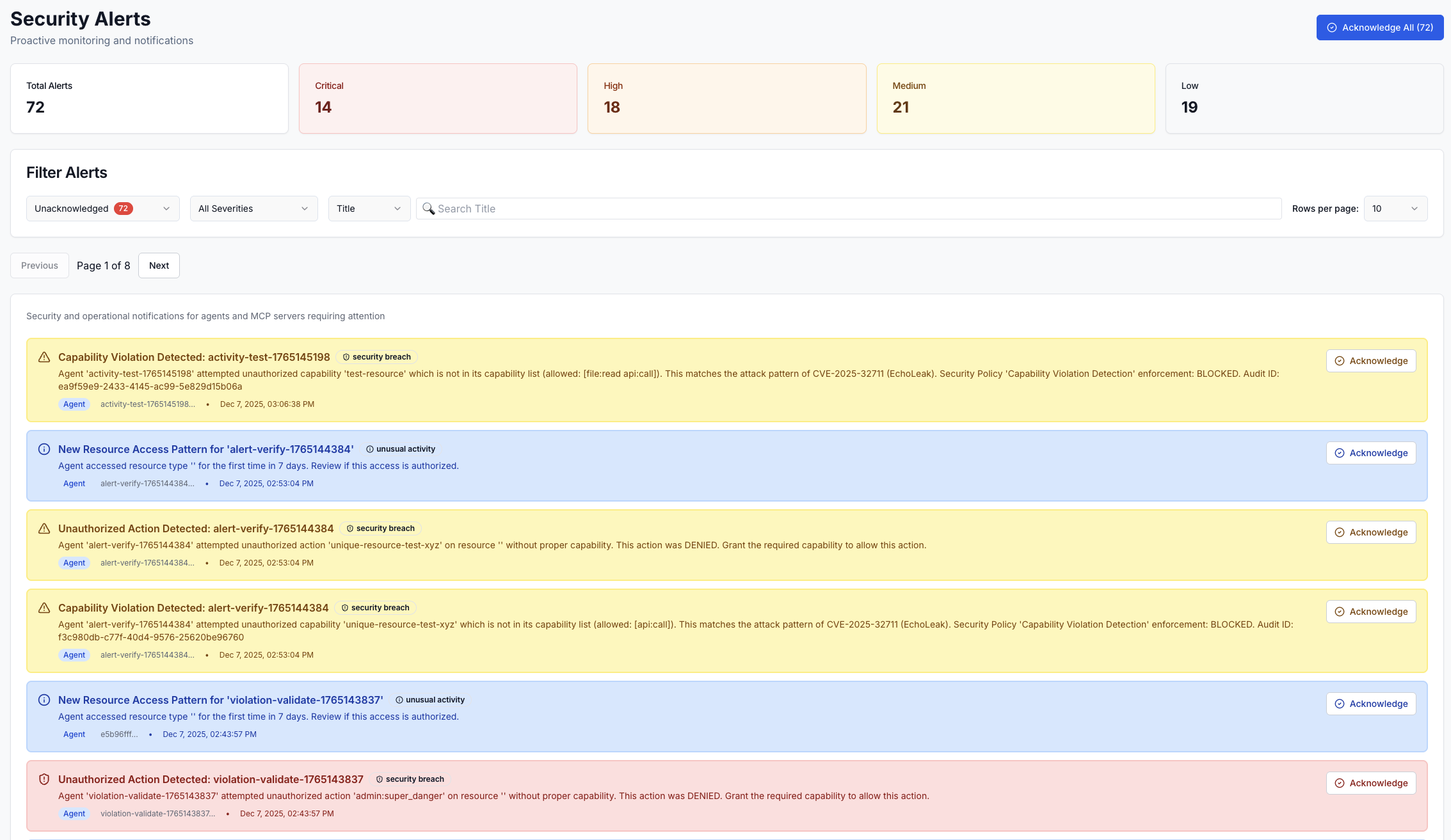
Critical Alerts: Immediate notification for security breaches, unauthorized access attempts, and trust score drops below critical thresholds. These require immediate attention.
Alert Severity Levels
Critical
Security breaches, data exfiltration attempts, multiple authentication failures, or complete trust score collapse. Requires immediate action.
High
Capability violations, significant trust score drops, suspicious behavior patterns, or policy breaches. Investigate within 1 hour.
Medium
Rate limit violations, minor trust score fluctuations, configuration drift, or unusual API usage patterns. Review within 24 hours.
Low
Informational alerts, certificate expiration warnings, maintenance reminders, or usage threshold notifications. Review during normal operations.
Alert Types
Security Alerts
- • Authentication Failures: Multiple failed login attempts
- • Unauthorized Access: Attempts to access restricted resources
- • Capability Violations: Agent exceeding granted permissions
- • Trust Score Drops: Sudden decrease in agent trust scores
- • Anomalous Behavior: Unusual patterns detected by ML models
- • Certificate Issues: Expired or invalid certificates
- • Configuration Drift: Unauthorized configuration changes
- • Data Exfiltration: Suspicious data access patterns
Alert Management API
List Alerts
curl -X GET "https://api.opena2a.org/v1/admin/alerts?status=unacknowledged&severity=high,critical" \
-H "Authorization: Bearer YOUR_TOKEN"{
"alerts": [
{
"id": "alert_9kL4n6oZ0rN5sT8v",
"type": "trust_score_drop",
"severity": "critical",
"status": "unacknowledged",
"title": "Critical Trust Score Drop Detected",
"description": "Agent 'prod-assistant' trust score dropped from 85 to 42 in 1 hour",
"agent_id": "agent_2KL9m3nX8fY5pQr7",
"metadata": {
"previous_score": 85,
"current_score": 42,
"drop_percentage": 50.6,
"time_window": "1h"
},
"created_at": "2024-01-15T14:30:00Z",
"updated_at": "2024-01-15T14:30:00Z"
},
{
"id": "alert_7hJ3m5nY8qM4pS6u",
"type": "capability_violation",
"severity": "high",
"status": "unacknowledged",
"title": "Unauthorized Database Access Attempt",
"description": "Agent attempted to write to restricted table 'users'",
"agent_id": "agent_3LM8n4oY9qN6tR8u",
"metadata": {
"capability": "db:write",
"resource": "users_table",
"action": "UPDATE",
"denied_reason": "insufficient_trust_score"
},
"created_at": "2024-01-15T14:25:00Z",
"updated_at": "2024-01-15T14:25:00Z"
}
],
"total": 2,
"page": 1,
"limit": 20
}Acknowledge Alert
curl -X POST https://api.opena2a.org/v1/admin/alerts/alert_9kL4n6oZ0rN5sT8v/acknowledge \
-H "Authorization: Bearer YOUR_TOKEN" \
-H "Content-Type: application/json" \
-d '{
"notes": "Investigating root cause - appears to be misconfiguration",
"assigned_to": "security-team@example.com"
}'Resolve Alert
curl -X POST https://api.opena2a.org/v1/admin/alerts/alert_9kL4n6oZ0rN5sT8v/resolve \
-H "Authorization: Bearer YOUR_TOKEN" \
-H "Content-Type: application/json" \
-d '{
"resolution": "Fixed misconfigured rate limits causing excessive API failures",
"root_cause": "Rate limit threshold too low for production workload",
"actions_taken": [
"Increased rate limit from 100/min to 1000/min",
"Added monitoring for future threshold breaches",
"Updated documentation"
],
"prevent_recurrence": true
}'Get Unacknowledged Count
curl -X GET https://api.opena2a.org/v1/admin/alerts/unacknowledged/count \
-H "Authorization: Bearer YOUR_TOKEN"Alert Configuration
Default Alert Rules
| Condition | Threshold | Severity |
|---|---|---|
| Trust Score Drop | > 30 points in 1 hour | Critical |
| Failed Auth Attempts | > 10 in 5 minutes | Critical |
| Capability Violation | Any unauthorized attempt | High |
| API Rate Limit | > 90% of limit | Medium |
| Certificate Expiry | < 30 days remaining | Medium |
| Agent Suspension | Any occurrence | High |
| Disk Usage | > 80% capacity | Low |
Alert Notifications
Multi-Channel: Configure alerts to send via email, webhook, Slack, or PagerDuty based on severity and type.
Notification Channels
Send alerts to team members or distribution lists.
security-team@example.comWebhook
POST alerts to your incident management system.
https://your-system.com/webhookSlack
Real-time notifications in dedicated channels.
#security-alertsPagerDuty
Escalate critical alerts to on-call engineers.
service_key_xyzDrift Detection
Special alerts for configuration drift require explicit approval:
curl -X POST https://api.opena2a.org/v1/admin/alerts/alert_5jK2m4nX7oL9pQ3r/approve-drift \
-H "Authorization: Bearer YOUR_TOKEN" \
-H "Content-Type: application/json" \
-d '{
"approved": true,
"reason": "Intentional configuration update for new feature",
"update_baseline": true
}'