JIT (Just-In-Time) Access
For sensitive operations, AIM supports real-time admin approval before execution. JIT access ensures that high-risk actions require human oversight, providing a critical security layer for destructive, financial, or privileged operations.
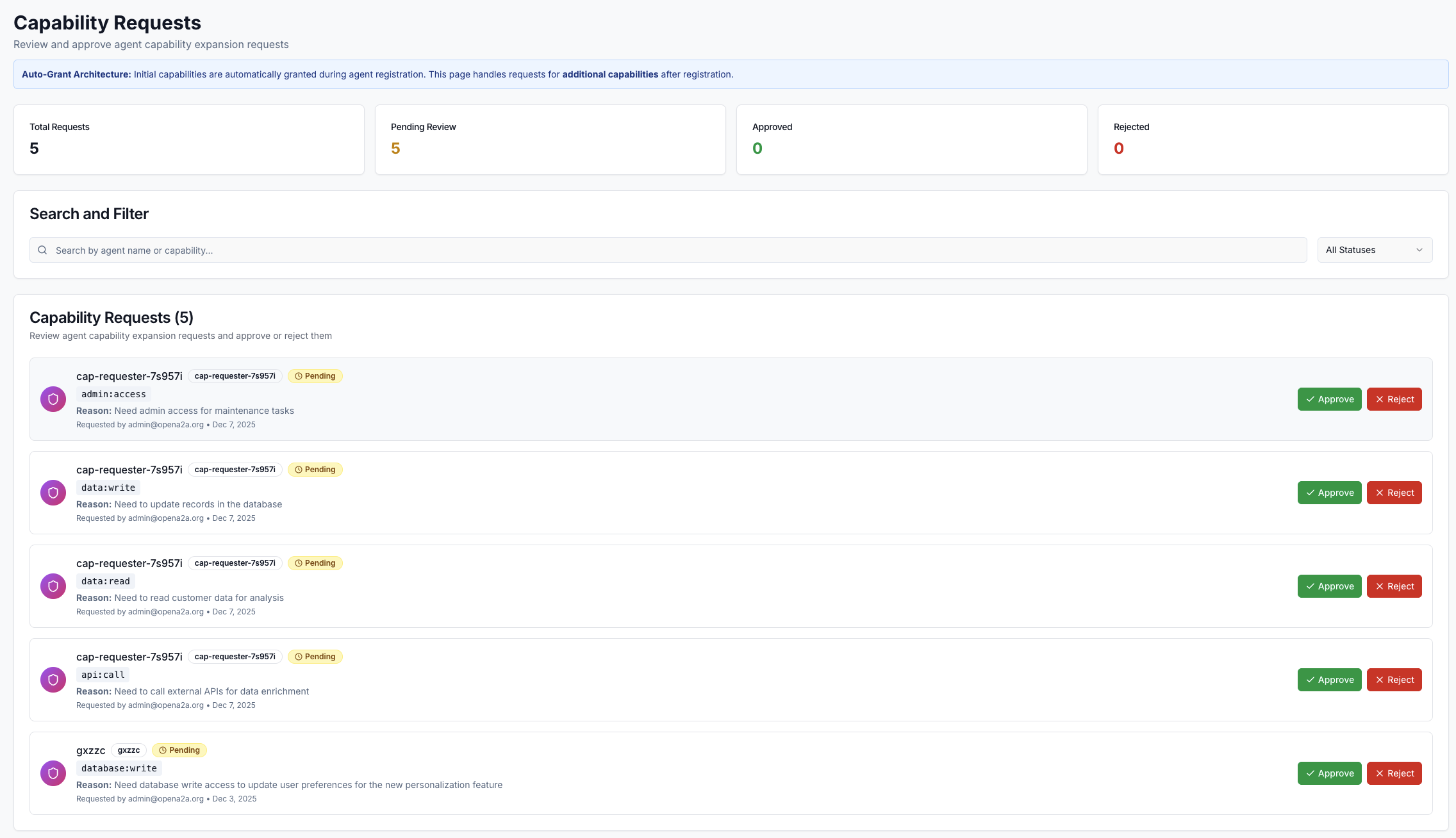
What is JIT Access?
JIT (Just-In-Time) Access is a security pattern where privileged operations are only permitted after explicit, time-limited approval. Instead of granting standing permissions, access is requested and approved in real-time.
Agent requests access when needed, not in advance
Approvals expire after configurable timeout
Full audit trail of requests, approvals, and outcomes
How JIT Access Works
Agent calls @agent.perform_action(..., jit_access=True) which creates a capability request
Request appears in admin's JIT Requests queue with agent, capability, resource, and context
Admin sees agent's trust score, capability history, and risk assessment before deciding
SDK receives decision, function executes (if approved) or raises JITDenied exception (if denied)
Who requested, who approved/denied, when, justification, and outcome are all recorded
When to Use JIT Access
High-Risk Operations
- • Database deletions - DROP TABLE, DELETE *
- • Data purging - Removing user data
- • Configuration changes - Production settings
- • Key rotation - Cryptographic materials
Financial Operations
- • Refunds - Processing customer refunds
- • Charges - One-time or unusual charges
- • Transfers - Moving funds between accounts
- • Subscription changes - Plan upgrades/downgrades
Privilege Escalation
- • Granting admin access - Elevating user roles
- • API key creation - Creating new credentials
- • Permission changes - Modifying RBAC
- • Service account creation - New identities
External Integrations
- • Third-party API calls - External services
- • Webhooks - Triggering external systems
- • Data exports - Sending data externally
- • Email/SMS - Customer communications
Best Practices
For Developers
- • Set appropriate timeouts for your use case
- • Always provide meaningful justification
- • Handle all exception types gracefully
- • Include relevant context in function args
- • Use JIT sparingly - only for truly sensitive ops
For Admins
- • Review trust score before approving
- • Check agent's capability history
- • Verify context matches legitimate use case
- • Always provide reason when denying
- • Monitor for unusual request patterns